
Expert Verified, Online, Free.

A company recently migrated all its workloads to the cloud and implemented a transit VPC with a managed firewall. The cloud infrastructure implements a 10.0.0.0/16 network, and the firewall implements the following ACLs: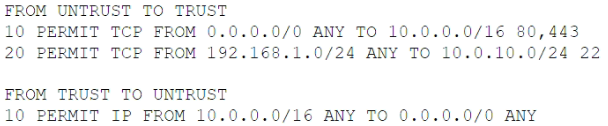
The Chief Information Security Officer wants to monitor relevant traffic for signs of data exfiltration. Which of the following should the organization place in its monitoring tool to BEST detect data exfiltration while reducing log size and the time to search logs?
YUYUY
5 months, 1 week agoarmid
2 days, 1 hour agoarmid
2 hours, 55 minutes agoCraZee
5 months, 1 week agoWhip
3 months, 3 weeks agotalosDevbot
5 months, 3 weeks agoPotato42
6 months, 2 weeks agosaucehozz
3 months ago[Removed]
7 months, 2 weeks agoguwno
6 months, 2 weeks agobiggytech
7 months, 3 weeks agonuel_12
7 months, 3 weeks ago