
Expert Verified, Online, Free.

Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
Correct Answer:
A
🗳️
Reference:
https://newbedev.com/chmod-u-x-versus-chmod-x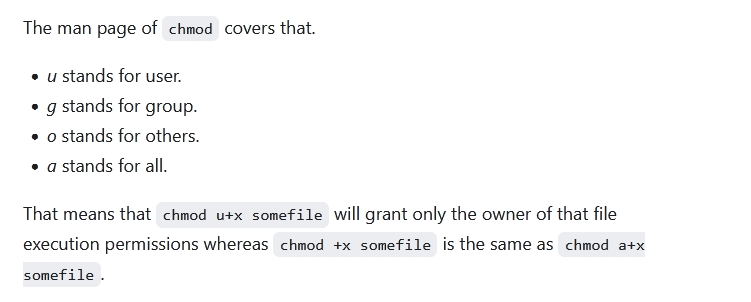
A penetration tester gains access to a system and establishes persistence, and then run the following commands:
Which of the following actions is the tester MOST likely performing?
Correct Answer:
C
🗳️
Reference:
https://null-byte.wonderhowto.com/how-to/clear-logs-bash-history-hacked-linux-systems-cover- your-tracks-remain-undetected-0244768/
A compliance-based penetration test is primarily concerned with:
Correct Answer:
C
🗳️
A penetration tester is explaining the MITRE ATT&CK framework to a company's chief legal counsel.
Which of the following would the tester MOST likely describe as a benefit of the framework?
Correct Answer:
A
🗳️
Reference:
https://attack.mitre.org/
Which of the following BEST describe the OWASP Top 10? (Choose two.)
Correct Answer:
AC
🗳️
Reference:
https://www.synopsys.com/glossary/what-is-owasp-top-10.html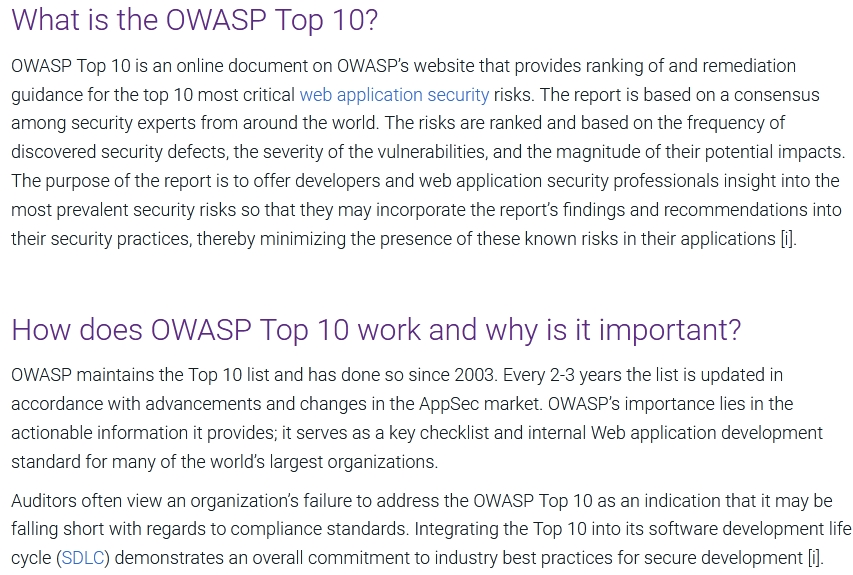
A penetration tester discovered a vulnerability that provides the ability to upload to a path via discovery traversal. Some of the files that were discovered through this vulnerability are:
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
Correct Answer:
C
🗳️
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
Correct Answer:
A
🗳️
A penetration tester ran the following command on a staging server: python -m SimpleHTTPServer 9891
Which of the following commands could be used to download a file named exploit to a target machine for execution?
Correct Answer:
D
🗳️
A penetration tester was able to gain access to a system using an exploit. The following is a snippet of the code that was utilized:
Which of the following commands should the penetration tester run post-engagement?
Correct Answer:
B
🗳️
Which of the following is MOST important to include in the final report of a static application-security test that was written with a team of application developers as the intended audience?
Correct Answer:
C
🗳️