
Expert Verified, Online, Free.

Which of the following is the software development process by which function, usability, and scenarios are tested against a known set of base requirements?
Correct Answer:
D
🗳️
A security analyst discovers the following firewall log entries during an incident:
Which of the following is MOST likely occurring?
Correct Answer:
C
🗳️
A security analyst is revising a company's MFA policy to prohibit the use of short message service (SMS) tokens. The Chief Information Officer has questioned this decision and asked for justification. Which of the following should the analyst provide as justification for the new policy?
Correct Answer:
D
🗳️
During an incident response procedure, a security analyst collects a hard drive to analyze a possible vector of compromise. There is a Linux swap partition on the hard drive that needs to be checked. Which of the following should the analyst use to extract human-readable content from the partition?
Correct Answer:
D
🗳️
A consultant is evaluating multiple threat intelligence feeds to assess potential risks for a client. Which of the following is the BEST approach for the consultant to consider when modeling the client's attack surface?
Correct Answer:
A
🗳️
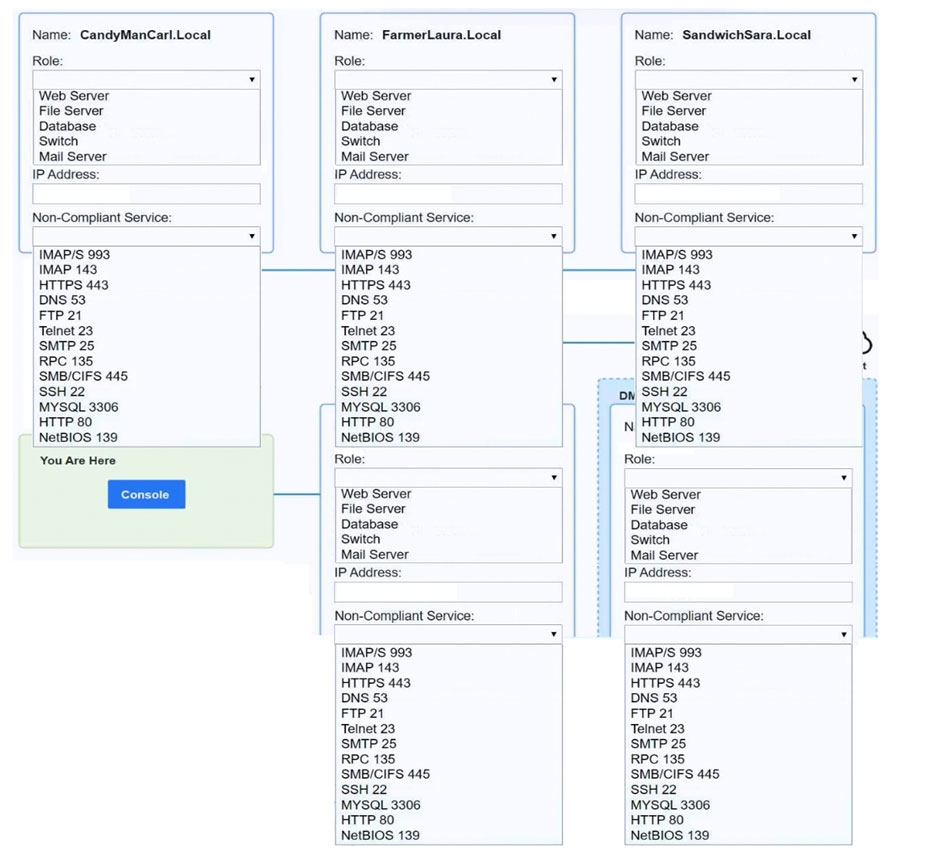
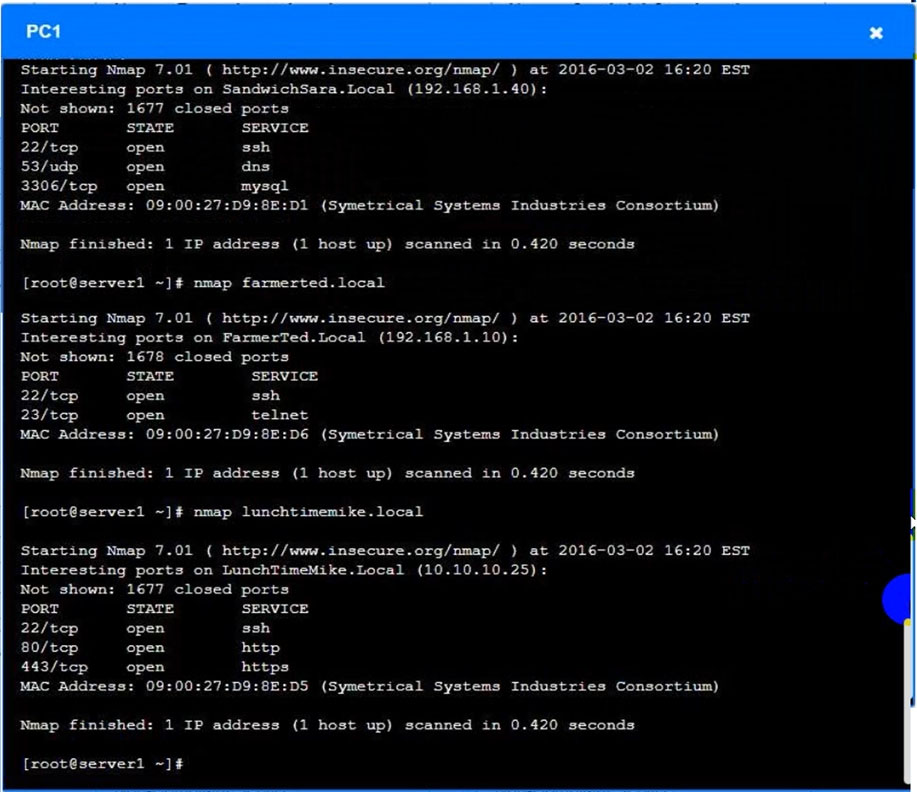
SIMULATION -
You are a penetration tester who is reviewing the system hardening guidelines for a company's distribution center. The company's hardening guidelines indicate the following:
✑ There must be one primary server or service per device.
✑ Only default ports should be used.
✑ Non-secure protocols should be disabled.
✑ The corporate Internet presence should be placed in a protected subnet.
INSTRUCTIONS -
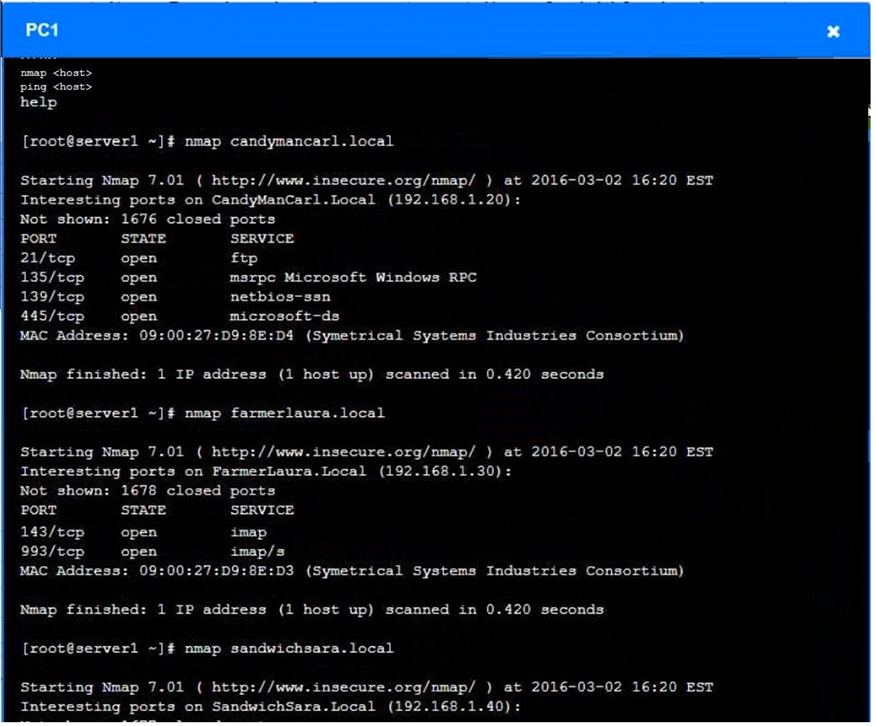
Using the tools available, discover devices on the corporate network and the services that are running on these devices.
You must determine:
✑ The IP address of each device.
✑ The primary server or service of each device.
✑ The protocols that should be disabled based on the hardening guidelines.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.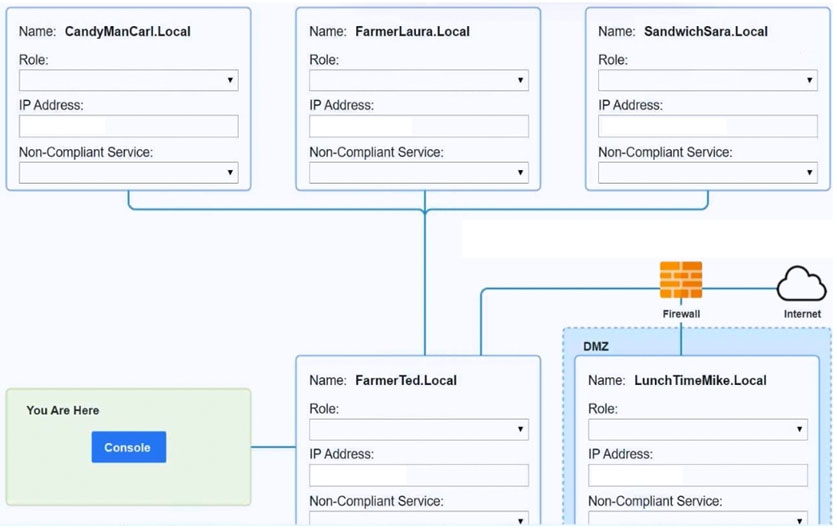
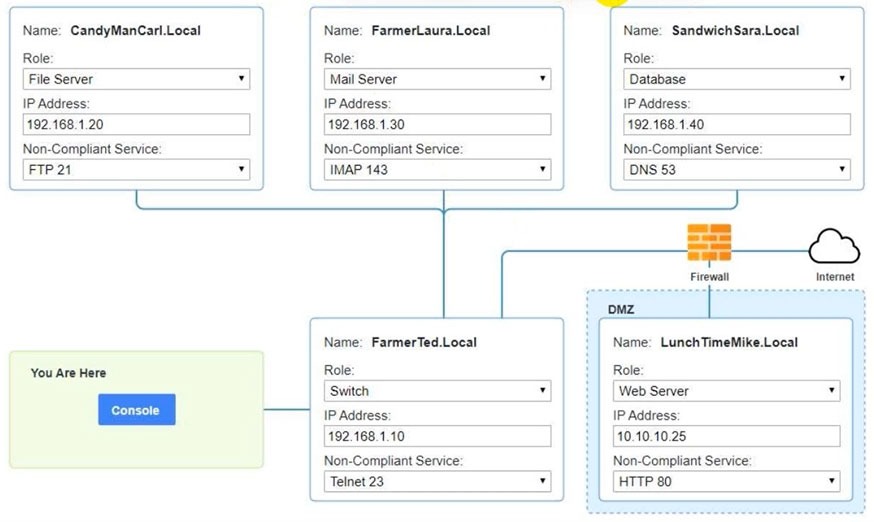
Correct Answer:
See explanation below.
A development team has asked users to conduct testing to ensure an application meets the needs of the business. Which of the following types of testing does this describe?
Correct Answer:
A
🗳️
An analyst receives artifacts from a recent intrusion and is able to pull a domain, IP address, email address, and software version. Which of the following points of the Diamond Model of Intrusion Analysis does this intelligence represent?
Correct Answer:
C
🗳️
While conducting a network infrastructure review, a security analyst discovers a laptop that is plugged into a core switch and hidden behind a desk. The analyst sees the following on the laptop's screen:
[*] [NBT-NS] Poisoned answer sent to 192.169.23.115 for name FILE-SHARE-A (service: File Server)
[*] [LLMNR] Poisoned answer sent to 192.168.23.115 for name FILE-SHARE-A
[*] [LLMNR] Poisoned answer sent to 192.168.23.115 for name FILE-SHARE-A
[SMBv2] NTLMv2-SSP Client : 192.168.23.115
[SMBv2] NTLMv2-SSP Username : CORP\jsmith
[SMBv2] NTLMv2-SSP Hash : F5DBF769CFEA7...
[*] [NBT-NS] Poisoned answer sent to 192.169.23.24 for name FILE-SHARE-A (service: File Server)
[*] [LLMNR] Poisoned answer sent to 192.168.23.24 for name FILE-SHARE-A
[*] [LLMNR] Poisoned answer sent to 192.168.23.24 for name FILE-SHARE-A
[SMBv2] NTLMv2-SSP Client : 192.168.23.24
[SMBv2] NTLMv2-SSP Username : CORP\progers
[SMBv2] NTLMv2-SSP Hash : 6D093BE2FDD70A...
Which of the following is the BEST action for the security analyst to take?
Correct Answer:
C
🗳️
A Chief Executive Officer (CEO) is concerned the company will be exposed to data sovereignty issues as a result of some new privacy regulations. To help mitigate this risk, the Chief Information Security Officer (CISO) wants to implement an appropriate technical control. Which of the following would meet the requirement?
Correct Answer:
B
🗳️